SmartConnect 2018
WCF REST Request Security
Request security allows the configuration of SmartConnect web service security to be used as standard across service requests, or specific to a single service request.
To define request security:
| • | To define standard request security select the 'Define Standard Security' button |
| • | To define security for a specific service request select the configuration button |
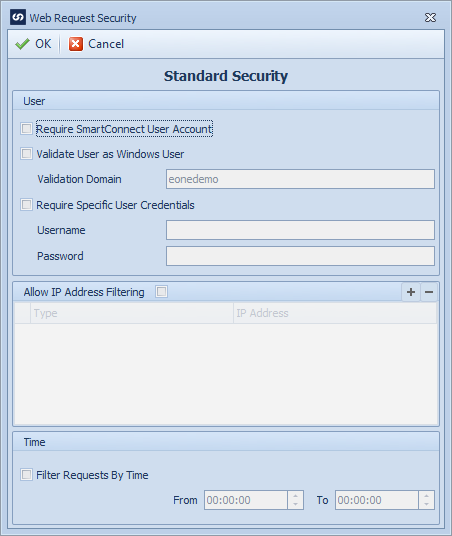
User request security:
The following options are available for validating users:
| • | Require SmartConnect User Account - Selecting this option will require the user name passed to the SmartConnect web service to match a user within SmartConnect. If this option is selected the username passed to the SmartConnect service should be domain/username as this is what is stored in SmartConnect for each user. If the request user fails this validation the client will receive an 'Invalid user for this operation' message, and 'Invalid user for this operation - invalid SmartConnect user' will be written to the security log. |
| • | Validate User as Windows User - selecting this option will require the user name and password passed to the SmartConnect web service to be validated against windows users. Validation occurs as follows: |
| o | If a validation domain has been selected in the security screen, the username and password will be validated against the specified domain. In this case if domain has been passed in with the username it will be ignored for this validation. |
| o | If no validation domain has been selected in the security screen, and a domain has been included with the username, the system will attempt to validate the username and password against the supplied domain. |
| o | If no domain has been selected in the security screen, an no domain was passed in with the username, the system will attempt to validate the username and password against the default domain used by the server. |
| o | If the request user fails this validation the client will receive an 'Invalid user for this operation' message, and 'Invalid user for this operation - invalid windows user' will be written to the security log. |
| • | Require Specific User Credentials - selecting this option will require the user connecting to the request to pass in the user credentials specified in the security screen. All other users attempting to connect will be rejected. If the request user fails this validation the client will receive and 'Invalid user for this operation' message, and 'Invalid user for this operation - specified credentials incorrect' will be written to the security log. |
IP filter request security:
| • | If requests should be filtered by IP address, select the checkbox at the top of the Allow IP Address Filtering group. Note: by default all IP addresses are automatically excluded when this option is selected. Valid IP addresses must be added to the filter grid. |
| • | The filter grid allows entry of both IPv4 and IPv6 addresses. Select the plus |
| • | Specific IP Addresses (e.g. 192.168.36.122) or IP Address ranges (e.g. 192.168.36.0/8) may be entered. |
Time filter request security:
If this request should only be available for a specific time range:
| • | Select the Filter Requests By Time checkbox |
| • | Select the from and to times |